|
1 | 1 | **NEW:** get the [JWT Handbook for free](https://auth0.com/e-books/jwt-handbook) and learn JWTs in depth! |
2 | 2 |
|
3 | 3 | ## What is JSON Web Token? |
4 | | -JSON Web Token (JWT) is an open standard ([RFC 7519](https://tools.ietf.org/html/rfc7519)) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the **HMAC** algorithm) or a public/private key pair using **RSA**. |
| 4 | +JSON Web Token (JWT) is an open standard ([RFC 7519](https://tools.ietf.org/html/rfc7519)) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the **HMAC** algorithm) or a public/private key pair using **RSA** or **ECDSA**. |
5 | 5 |
|
6 | 6 | Although JWTs can be encrypted to also provide secrecy between parties, we will focus on *signed* tokens. Signed tokens can verify the *integrity* of the claims contained within it, while encrypted tokens *hide* those claims from other parties. When tokens are signed using public/private key pairs, the signature also certifies that only the party holding the private key is the one that signed it. |
7 | 7 |
|
8 | 8 | Let's explain some concepts further. |
9 | 9 |
|
10 | 10 | - **Compact**: Because of their smaller size, JWTs can be sent through a URL, POST parameter, or inside an HTTP header. Additionally, the smaller size means transmission is fast. |
11 | 11 |
|
12 | | -- **Self-contained**: The payload contains all the required information about the user, avoiding the need to query the database more than once. |
| 12 | +- **Self-contained**: The payload may contain extra information about the user, avoiding the need to query the database more than once. |
13 | 13 |
|
14 | 14 | ## When should you use JSON Web Tokens? |
15 | 15 | Here are some scenarios where JSON Web Tokens are useful: |
@@ -48,7 +48,7 @@ Then, this JSON is **Base64Url** encoded to form the first part of the JWT. |
48 | 48 |
|
49 | 49 | ### Payload |
50 | 50 |
|
51 | | -The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically, the user) and additional metadata. |
| 51 | +The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically, the user) and additional data. |
52 | 52 | There are three types of claims: *registered*, *public*, and *private* claims. |
53 | 53 |
|
54 | 54 | - [**Registered claims**](https://tools.ietf.org/html/rfc7519#section-4.1): These are a set of predefined claims which are not mandatory but recommended, to provide a set of useful, interoperable claims. Some of them are: **iss** (issuer), **exp** (expiration time), **sub** (subject), **aud** (audience), and [others](https://tools.ietf.org/html/rfc7519#section-4.1). |
@@ -99,18 +99,15 @@ If you want to play with JWT and put these concepts into practice, you can use [ |
99 | 99 | 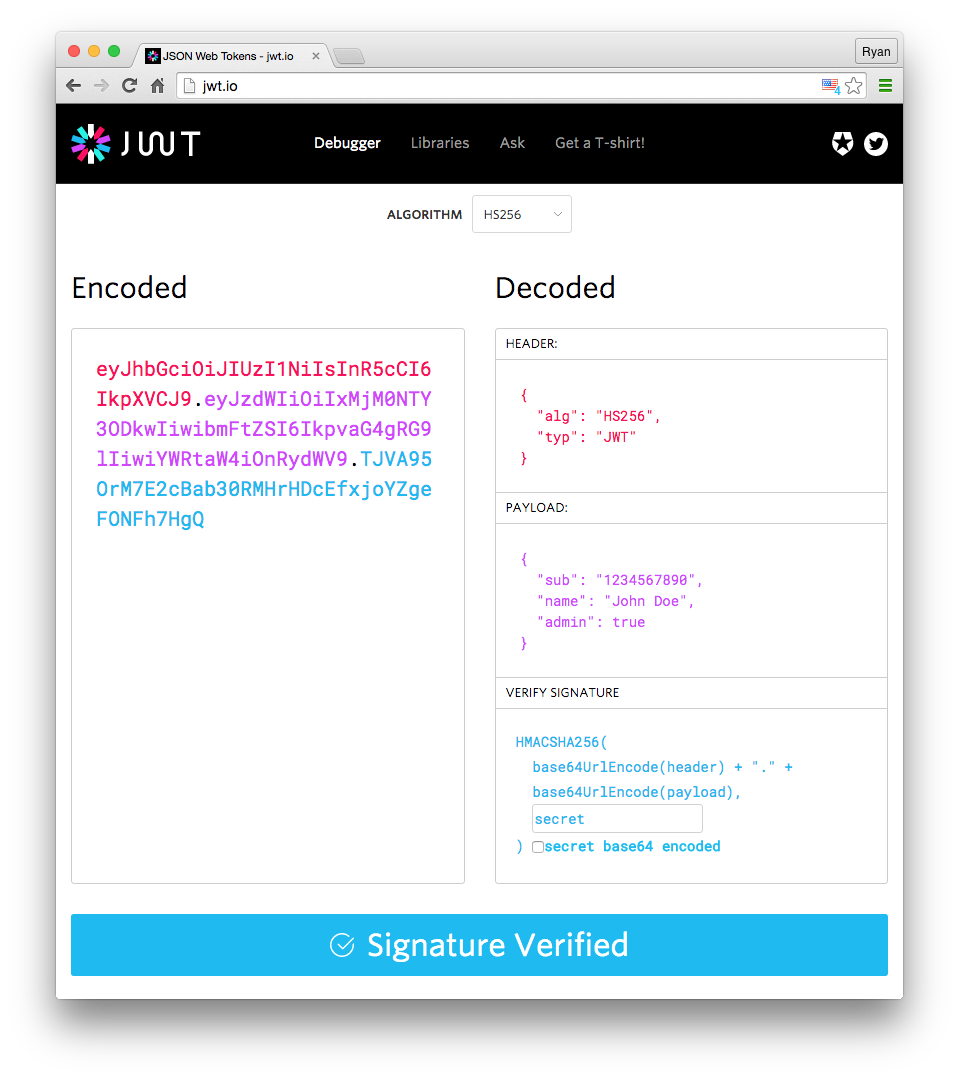 |
100 | 100 |
|
101 | 101 | ## How do JSON Web Tokens work? |
102 | | -In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned and must be saved locally (typically in local storage, but cookies can be also used), instead of the traditional approach of creating a session in the server and returning a cookie. |
103 | | - |
104 | | -> There are security considerations that must be taken into account with regards to the way tokens are stored. These are enumerated in [Where to Store Tokens](https://auth0.com/docs/security/store-tokens). |
| 102 | +In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Since tokens are credentials, great care must be taken to prevent security issues. In general, you should not keep tokens longer than required. |
105 | 103 |
|
106 | 104 | Whenever the user wants to access a protected route or resource, the user agent should send the JWT, typically in the **Authorization** header using the **Bearer** schema. The content of the header should look like the following: |
107 | 105 |
|
108 | 106 | ``` |
109 | 107 | Authorization: Bearer <token> |
110 | 108 | ``` |
111 | 109 |
|
112 | | -This is a stateless authentication mechanism as the user state is never saved in server memory. |
113 | | -The server's protected routes will check for a valid JWT in the Authorization header, and if it's present, the user will be allowed to access protected resources. As JWTs are self-contained, all the necessary information is there, reducing the need to query the database multiple times. |
| 110 | +This can be, in certain cases, a stateless authentication mechanism. The server's protected routes will check for a valid JWT in the `Authorization` header, and if it's present, the user will be allowed to access protected resources. If the JWT is self-contained, all the necessary information is there, reducing the need to query the database multiple times. |
114 | 111 |
|
115 | 112 | This allows you to fully rely on data APIs that are stateless and even make requests to downstream services. It doesn't matter which domains are serving your APIs, so Cross-Origin Resource Sharing (CORS) won't be an issue as it doesn't use cookies. |
116 | 113 |
|
|
0 commit comments