You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: views/md/introduction.md
+10-13Lines changed: 10 additions & 13 deletions
Original file line number
Diff line number
Diff line change
@@ -33,13 +33,12 @@ The header *typically* consists of two parts: the type of the token, which is JW
33
33
34
34
For example:
35
35
36
-
```js
36
+
``
37
37
{
38
38
"alg": "HS256",
39
39
"typ": "JWT"
40
40
}
41
-
42
-
```
41
+
``
43
42
44
43
Then, this JSON is **Base64Url** encoded to form the first part of the JWT.
45
44
@@ -58,14 +57,13 @@ There are three types of claims: *reserved*, *public*, and *private* claims.
58
57
59
58
An example of payload could be:
60
59
61
-
```js
60
+
``
62
61
{
63
62
"sub": "1234567890",
64
63
"name": "John Doe",
65
64
"admin": true
66
65
}
67
-
68
-
```
66
+
``
69
67
70
68
The payload is then **Base64Url** encoded to form the second part of the JSON Web Token.
71
69
@@ -74,12 +72,12 @@ To create the signature part you have to take the encoded header, the encoded pa
74
72
75
73
For example if you want to use the HMAC SHA256 algorithm, the signature will be created in the following way.
76
74
77
-
```js
75
+
``
78
76
HMACSHA256(
79
77
base64UrlEncode(header) + "." +
80
78
base64UrlEncode(payload),
81
79
secret)
82
-
```
80
+
``
83
81
84
82
The signature is used to verify that the sender of the JWT is who it says it is and to ensure that the message was't changed in the way.
85
83
@@ -99,7 +97,9 @@ In authentication, when the user successfully logs in using his credentials, a J
99
97
100
98
Whenever the user wants to access a protected route or resource, it should send the JWT, typically in the **Authorization** header using the **Bearer** schema. Therefore the content of the header should look like the following.
101
99
102
-
`Authorization: Bearer <token>`
100
+
``
101
+
Authorization: Bearer <token>
102
+
``
103
103
104
104
This is a stateless authentication mechanism as the user state is never saved in the server memory.
105
105
The server's protected routes will check for a valid JWT in the Authorization header, and if there is, the user will be allowed. As JWTs are self-contained, all the necessary information is there, reducing the need of going back and forward to the database.
@@ -125,8 +125,5 @@ Regarding usage, JWT is used at an Internet scale. This highlights the ease of c
125
125
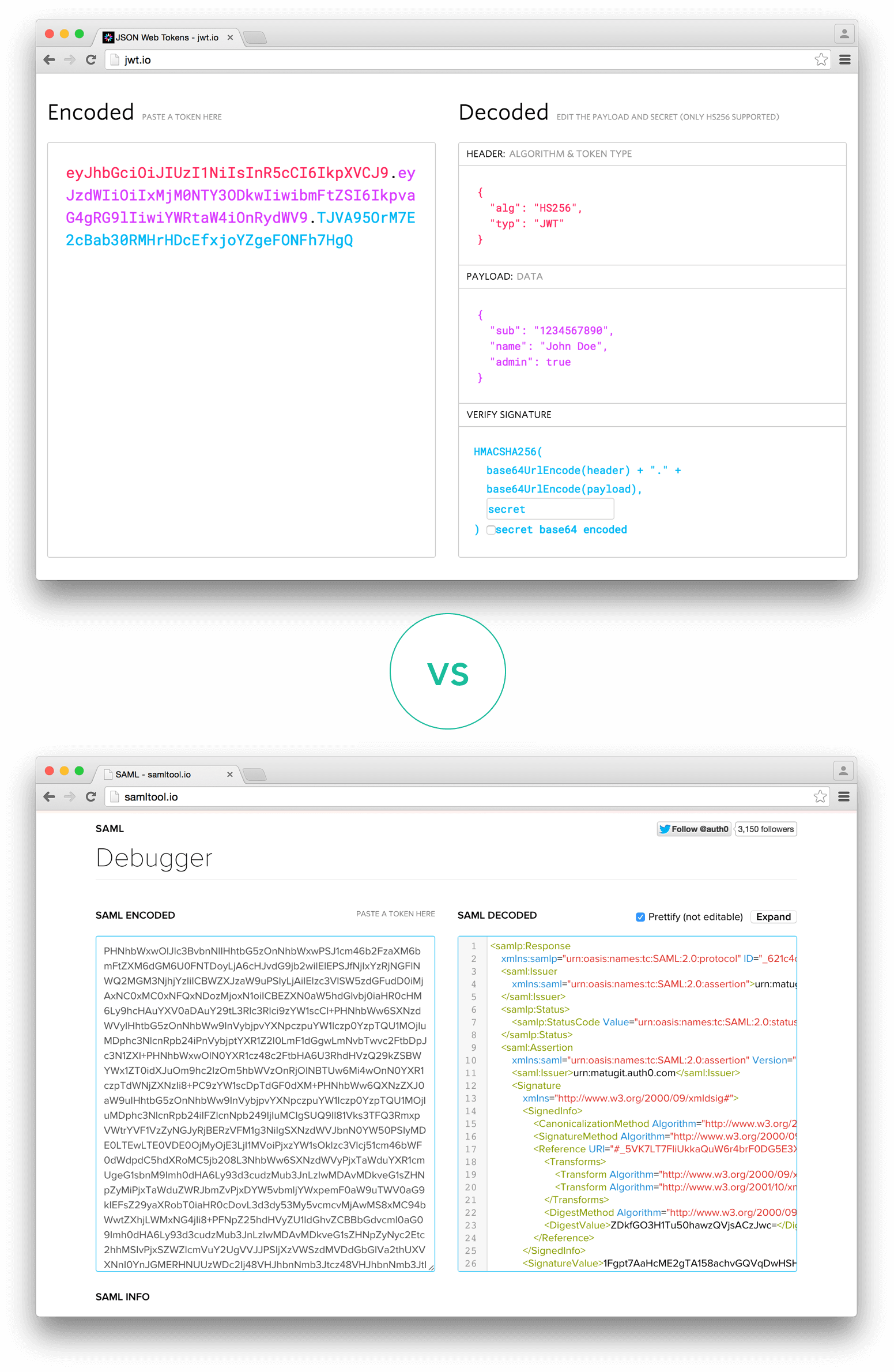
126
126
_Comparison of the length of an encoded JWT and an encoded SAML_
127
127
128
-
##How we use JSON Web Tokens in Auth0?
129
-
130
-
In Auth0, we issue JWTs as a result of the authentication process. When the user logs in using Auth0, a JWT is created, signed, and sent to the user. Auth0 supports signing JWT with both HMAC and RSA algorithms. This token will be then used to authenticate and authorize with APIs which will grant access to their protected routes and resources.
131
128
132
-
We also use JWTs to perform authentication and authorization in Auth0's API v2, replacing the traditional usage of regular opaque API keys. Regarding authorization, JSON Web Tokens allow granular security, that is the ability to specify a particular set of permissions in the token, which improves debuggability.
129
+
If you want to read more about JSON Web Tokens browse to the [JSON Web Token landing page](auth0.com/learn/json-web-tokens)in Auth0.
0 commit comments